Penetration testing is a testing technique where people who were not involved in software development are hired to gain access into the software by hacking it. This process gives the company an idea of how hackers may breach the software security and the possible loopholes to work on.
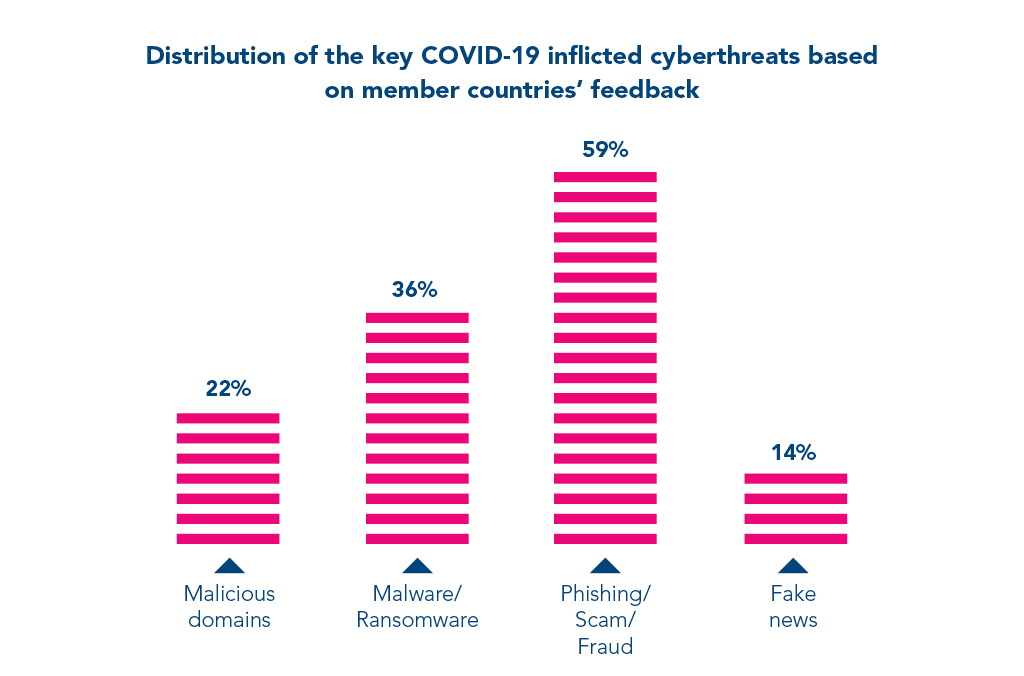
According to 2019, Trustwave reports 100% of tested web software had at least one vulnerability, making it the second straight year of record. In fact, INTERPOL reports show that 907 000 spam messages and 737 malware incidents have been recorded between January and April in 2020. The point?
Quality penetration and security testing should give you a deep insight into your organization’s overall security posture, and they also help a company stay prepared against hackers and security breaches.
More importantly, effective penetration testing should be carried out by qualified and trusted professionals, preferably those who have degrees in cybersecurity or hacking, and certified penetration testers. You have to ask some questions during the interview process to hire the best penetration tester and sieve out the inexperienced or unqualified candidates properly.
We outlined these specific 30+ penetration testing interview questions and answers based on our experience of providing penetration testing services to our clients and recruiting penetration testers.
Before you start reading further, you might want to check out what is penetration testing to gain a broader scope of the topic.
Let’s begin.
1. Describe What Information Security Is All about
Information Security can be described as the protection of all the data associated with the software. It is the process of putting measures in place to ensure that all the data related to software does not get into the wrong hands or does not get leaked to the general public. An unsecured software is a considerable risk to both the development company and the end-users.
Conducting tests such as penetration testing can help a company understand how secure their information is and fortify loopholes. The security of every info coming in and going out of your software must be guaranteed before launching it to the general public.
2. Explain the Advantages of Penetration Testing
As briefly explained earlier, penetration testing helps a company stay prepared against hackers and security breaches by exposing security loopholes and unforeseen errors that were not identified during the development process. It gives a company extra protection against possible future attacks.
Penetration testing guarantees all the information within the software by ensuring that the data bank is secured. Apart from protection against hackers’ attacks, penetration testing helps a company quickly identify other errors such as bugs, viruses, glitches, etc.
| Recommend read: Most expensive software bugs in history. |
3. Explain Symmetric and Asymmetric Encryption
Firstly, encryption is changing the order of data’s appearance from its original format to keep out intrusion from those who do not have the clearance to access the data. Symmetric encryption involves the use of a single encryption and decryption pass key. One password can both encrypt and decrypt the data in such cases, and both the owner and end-user share the same key.
In asymmetric encryption, the software owners have a private passkey while the end-users have a public pass key. This is to segregate high-level data that the public cannot access from available data.
4. Explain the Term “Vulnerability”
The vulnerability of software is the condition of being prone to attacks from hackers or the state of not staying completely secure. Vulnerable software has some security defects that can be exploited by fraudulent people to gain access to the software and cause havoc.
In some cases, individuals without ulterior motives may stumble upon such vulnerabilities, and they may mistakenly expose intellectual properties, private information, or merely the data bank. A vulnerable software must undergo penetration testing to ascertain all the vulnerabilities.
5. Talk about Your Penetration Testing Experience
The candidate should be able to explain the previous penetration tests he/ she carried out. Every detail is essential, such as the type of software that was tested, the penetration testing technique used, how difficult or easy the test was, the time it took to complete the test, the discovered vulnerabilities, how the vulnerabilities were corrected, etc.
It is important not to push the candidate to reveal any non-disclosure agreement signed with a previous employer. The candidate’s experience level should give you an idea of what he/ she will bring to your company if hired.
6. Explain How Data Is Protected During and after Penetration Testing
Before commencing a penetration test, all the data associated with the software must be carefully backed up because the test can affect the data to prove the software’s vulnerability. Protecting data is a priority before, during, and also after penetration testing. Data can be backed up by either storing copies in the cloud or directly into an external secure hard drive or setting up private encryption. The whole idea is to have a replacement for your data in case of any damage.
7. Explain the Term “Intrusion Detection”
Intrusion Detection is the process of finding out an external influence trying to gain illegal access into a software. As its name implies, any form of unlawful access is discovered and reported for necessary action to be taken against the intrusion. It’s like the technology that detects burglary and sounds the alarm. During penetration testing, the company will automatically determine whether the intrusion detection technology in its software is functioning correctly.
8. What Are the Possible Causes of Security Vulnerabilities?
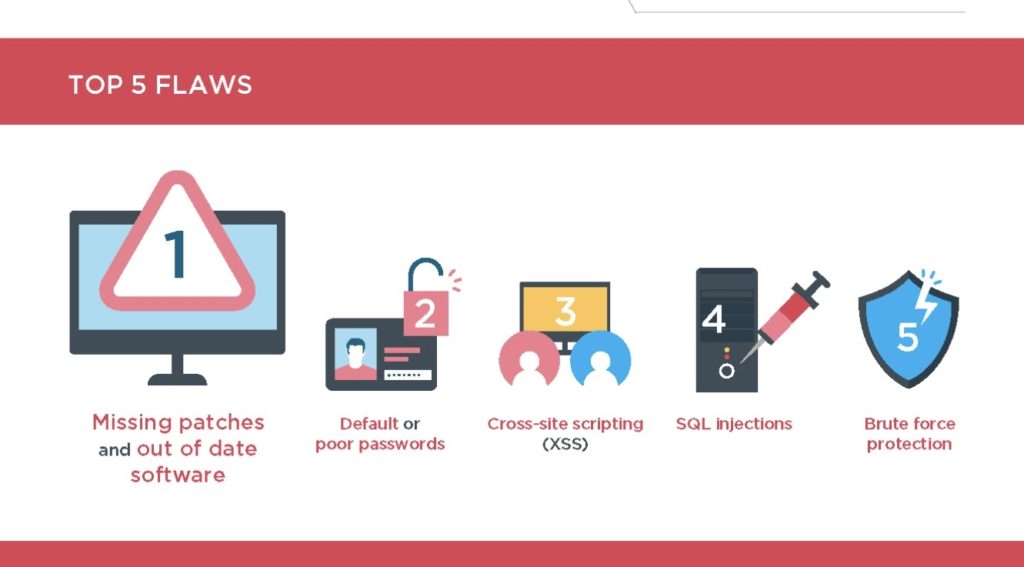
The software may be classified as vulnerable for various reasons. Most of the time, it is the penetration testers’ role to determine the vulnerability level of the software. Erroneous programming can make software vulnerable. Lack of proper private and public encryption can make software vulnerable. Lack of adequate intrusion detection systems. Lack of appropriate surveillance systems. When the software’s data are not adequately backed up or protected, the software can be classified as vulnerable.
9. Advantages of Intrusion Detection Systems
An intrusion detection system helps a company to know when hackers try to gain access to their software. It keeps the company ready at all times to swing into action as soon as there is an attempted breach. Hackers are discouraged from gaining access to the software when they find out that intrusion detection systems are in place. It gives software extra protection from intrusion, and some high-level intrusion detection systems can point out the exact location and device from where the intrusion took place. This ensures quick identification and arrest of the culprits.
10. Explain SSL/TLS
TLS stands for Transport Layer Security while SSL stands for Secure Sockets Layer. It is important to note that TLS is an upgraded version of SSL, which is meant to carry out similar functions. They are supposed to protect the transmission of data of any kind between web browsers and web application owners. SSL/TLS ensures the security of communication, images, videos, text, encrypted files, etc. by creating a confidential route between those providing the data and those receiving it.
11. Explain How Risk Analysis and Penetration Testing Are Different from Each Other
Risk analysis is merely studying all the possible errors that may cause problems in the software, while penetration testing is the process of legally attacking the system to discover the vulnerabilities of the software. Risk analysis is a more economical approach to solving problems, while penetration testing takes a more technical approach. Risk analysis can be carried out by a finance expert who has some probability skills, while penetration testing requires a skilled information technology expert in computer programming and preferably hacking. Risk analysis is more speculative, while penetration testing involves actual work.
12. Explain the Tools You Will Use for Penetration Testing
Penetration testing requires high-level computer systems, operating systems, graphic cards, and certain software that can be used for high-level hacking. Some of the effective tools every penetration tester should have include:
- Burp suite (both the free and commercial versions are available);
- Nessus (both free and commercial versions are available); Wireshark (open source);
- Metasploit (open source);
- NMap (open source);
- OpenVAS (open source);
- Nikto (open source);
- OWASP ZAP (open source).
Some of these tools require extensive training, and some come with certifications.
13. A Penetration Test Takes How Long to Be Completed?
The length of time it would take to complete a penetration test depends on some factors such as the nature of the software being tested, the size of the software, its vulnerability level, the level of security of the software, the experience level of the penetration tester, the software being used for the test, the technique of the test (either automated or manual), etc. These factors will determine how fast or how slow the test will go. For instance, if the software is enormous, expect the penetration test to take more time than when a smaller software is being tested.
14. Does Penetration Testing Break a System?
The primary purpose of Penetration Testing is to break software in some way or another. By the break, we mean breaking it up for unauthorized accessibility, which may lead to damages. That is why it is highly advisable to backup the data associated with the software before starting a penetration test because the test might damage some of the software’s data. Therefore to answer the question, Yes! Penetration testing can break a system.
15. Do You Have Any Penetration Testing Certification?
Some notable certificates that may demonstrate a candidate’s level of knowledge concerning penetration testing include EC-Council Certified Ethical Hacker (CEH); GIAC Exploit Researcher & Advanced Penetration Tester (GXPN); and Offensive Security Certified Professional (OSCP).
Although, in some cases, certifications can be an added advantage; however, further inquiries have proved that many candidates without any certification can be better than those with certificates. It is better to dwell on asking a candidate for more details concerning carrying out actual tests. If the candidate has some certifications, you can then probe deeper by asking him/ her more questions concerning the certificate to know if it will add value to your intended penetration test.
16. Do I Still Need Penetration Testing Although My Data Is in the Cloud?
Of course! The fact that all your data is in the cloud does not mean that they cannot be hacked into. No matter how secure you feel that your software is, you have to put it through rigorous penetration testing. Ethical hackers have to mimic the fraudulent hackers out there to prepare and fortify your software against the worst possible attack. The most recent hacks are taking place via the cloud. Thus, online storage can also be vulnerable.
17. Outline the Systems on Which Penetration Testing Can Be Performed
Although we have been entirely focused on using the term software to generalize, penetration testing can be carried out on various systems such as web applications, servers, mobile devices, endpoints, computers, wireless networks, cloud services, network devices, hardware systems, programmable controllers, complex systems, databases, mobile applications, websites, internet services, browsers, virtual private networks (VPN), public networks, transmission technologies, transmission towers, satellite communication systems, network receivers, storage systems, etc.
Anything that can be hacked can and should go through penetration testing to attain a higher level of security. In the course of this article, we may use the term system, software, or product when describing platforms on which penetration testing can be carried out.
18. Should Penetration Testing Be a Routine Test?
The simple answer to this question is Yes! Penetration testing should be a routine test that can be done just before the product is launched, after a minor or major update, after the intrusion detection system detects an intrusion, when developing a different version, etc. Some companies also conduct penetration tests periodically, like 3 to 4 times annually to stay ahead of potential threats.
Change is constant, and therefore the dangers posed today might not be the dangers faced tomorrow, this is why penetration testing should be carried out routinely. It’s a continuous process that never ends as long as the product remains active.
19. Can Penetration Testing Disrupt a Company’s Network of Operations?
Just like in the case of whether penetration testing can break a system, in this case, it is crucial to understand that penetration testing can disrupt an organization’s network of operation. Look at it this way, just like a hack into the organization’s software can disrupt its operations, so also can penetration testing cause disruption. Penetration testing is simply legalized hacking, so those who carry out penetration tests are sometimes referred to as Ethical Hackers.
20. What’s Different between Penetration Testing and Security Testing?
Security testing is a broader term. While penetration testing only involves using external experts to attack the system or software to ascertain how secure it is, security testing consists of guarding the system or software by developing and testing various security measures.
| Penetration Testing | Security Testing |
|---|---|
| Intrusive form of testing | Non-intrusive form of testing |
| Narrow focus | Wide focus |
| Heavy use of security tools | Combined interviews and tools |
21. Is Penetration Testing Still Important If the Company Has a Firewall?
Simply put, penetration testing is still necessary whether the company has a firewall or not because hackers do not care if a company has a firewall or not before trying to gain unauthorized access. Hackers can bypass a firewall, or sometimes the firewall may just be damaged, so it is vital to ascertain the firewall’s condition through penetration testing.
22. Why Should Penetration Testing Be Carried out by a Third Party?
Penetration testing should be carried out by a third party with little or no knowledge of how the software was developed. He/ she should not be someone involved in the development process of the software. This ensures that the ethical hacker mimics the exact approach a fraudulent hacker will take in trying to gain unauthorized access into the system. Simply put, a fraudulent hacker is most likely someone who wasn’t involved in developing the system; therefore, the ethical hacker shouldn’t be either.
23. What Are the Legal Steps Involved in Penetration Testing?
Before penetration testing commences, the ethical hacker must sign a non-disclosure agreement with the company to ensure the confidentiality of all the data associated with the company.
24. Can Penetration Testing Be Automated?
Some systems can be programmed to try to automatically study the architecture of a system and try to break into it. Such systems can either be used in place of human ethical hackers or utilized together with ethical hackers.
25. Explain the Term “Threat Modelling”
Threat modeling is simply the process of analyzing the possible threats and vulnerabilities within a system. It involves identifying the hazards, carefully studying them, and correcting them accordingly.
26. Explain the Term “File Enumeration”
File enumeration, as its name implies, is the process of shedding more light on the files within a database. It gives the organization and the ethical hacker a complete description, function, location, and the type of data within a system.
27. Explain the Phases of Penetration Testing
Penetration testing involves various effective techniques. One of the most effective tactics involves the following phases:
- Analysing the system that is to be tested.
- Backing up all the data associated with the system.
- Carrying out threat modeling.
- Trying to hack the system.
- Analysing the vulnerability and loopholes that were identified
- Correcting all the issues encountered and setting up an intrusion detector.
- Documenting the whole process from top to bottom
- Scheduling a standard penetration testing package.
28. Explain the Most Difficult Penetration Test You Have Experienced
The candidate should be able to explain the toughest penetration test he/ she had to carry out. This will help you understand their breaking points and help you know whether they could improve their skills based on the difficulty encountered. You will be able to discover their strengths, weaknesses, and personal upgrades.
29. Outline the Full Meanings of 2FA, 2S2D, 2VPCP, 3DES, 3DESE, And 3DESEP
- 2FA: Two Factor Authentication
- 2S2D: Double-Sided Double-Density
- 2VPCP: Two-Version Priority Ceiling Protocol
- 3DES: Triple Data Encryption Standard
- 3DESE: Triple Data Encryption Standard Encryption
- 3DESEP: Triple Data Encryption Standard Encryption Protocol
30. Explain the Term “STRIDE”
STRIDE is an abbreviation used to identify a thread modeling technique.
- The S stands for Spoofing.
- The T stands for Tampering.
- The R stands for Repudiation.
- The I stands for Information disclosure.
- The D stands for Denial of Service (DoS).
- The E stands for: Elevation of privilege.
- To correctly identify, analyze, and correct the threats to a system, a company must adopt the above threat modeling technique.
31. Why Should We Hire You?
Here, the candidate has to identify their strengths and whatever makes him/ her better than the rest. They should be able to make a compelling explanation highlighting why hiring them would add value to your company.
To Sum up
An organization that doesn’t test regularly may not identify the weaknesses in their security systems or software prone to external threats and exploits. Therefore, it is highly recommended for every organization to undergo complete security testing, including penetration testing, to give an accurate internal and external security review.
Outsourcing to the right penetration QA team will further bolster the best security practices you may already have in place. If you’re interested in hiring an entire QA team, and not only ethical hackers, check out our blog post on Top 50 software testing interview questions and answer Let’s know if you have more security questions or you want to get an estimate of your project.









great